“With technology making lives easy day by day, cybercriminals too are finding innovative ways to get into our lives. Along with the ease of access, security and privacy are also imperative in this digital age, where our lives are connected with IoT devices.” (CisoMag, 2019)
Artificial Intelligence and machine learning are now becoming essential to information security because these technologies are capable of swiftly analysing millions of data sets and tracking down a wide variety of cyber threats that may result in a phishing attack. Phishing is the means of stealing login credentials or credit card numbers. It often comes from fake email links or fraudulent text messages, e.g. AIB scam text messages.
There are two types of cyber crime targets; Hard infrastructure- defence installations, nuclear facilities, electrical and telecommunications network, manufacturing plants. Soft infrastructure- banks, private firms, public record systems, health and insurance record systems. Attacking hard targets aims to cripple essential infrastructure within an industry or society, however, attacking soft targets aims to disrupt, embarrass or punish firms.
Hackers are turning to Artificial Intelligence and using it to weaponise malware and attacks to counter the advancements made in cybersecurity solutions. Hackers program codes to execute at a specific time and date after an application has been installed or when a targeted number of users have subscribed to the application. This is to maximise the impacts the attacks will cause.
If an activity is central to a persons identity (e.g. driving, playing sports, cooking), then they are less likely to adopt artificial intelligence during their personal activities. For example, people would rather read from a recipe book then have a smart home device read it for them. Women tend to perceive more risk generally and are more risk averse than men and are therefore less likely to adopt artificial intelligence than men.
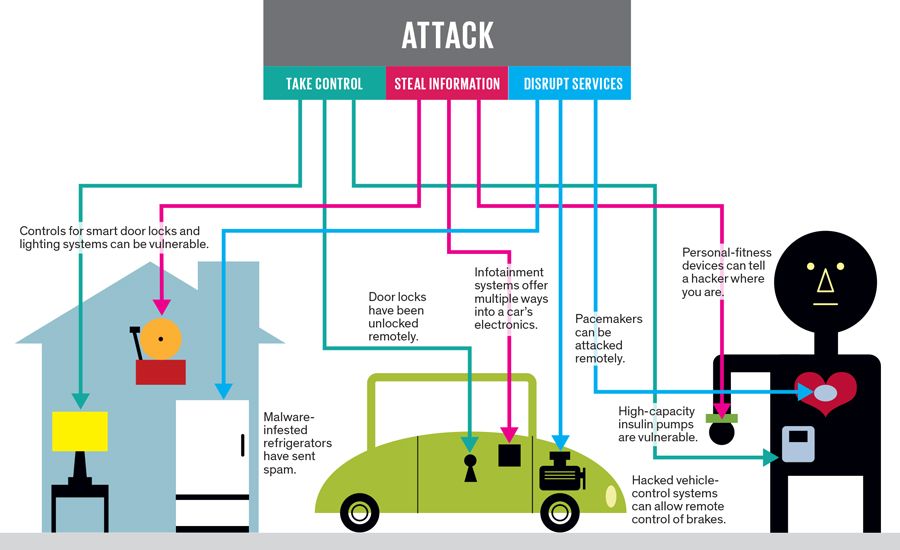
The irony, of course, is that artificial intelligence begins with human input and programming and is then manipulated by humans or by the programme itself. For example, to speak more about artificial intelligence in the home, in 2020 there were multiple reports of people hacking into the Amazon Ring doorbell. Ring is a home security company that was acquired in 2018 by Amazon. They sell devices from a $34 flood alarm to a $499 doorbell that allows users to see, hear and speak to visitors. While the Ring gadget is designed to make people feel safer in their homes, the people connected to this particular lawsuit have stated that it put their families at risk. The unknown voice commented on the kids’ basketball game and encouraged them “to get closer to the camera,” according to the lawsuit. (Evans, 2020). Below is an example of how your smart home devices may be affected with the possibility of being hacked, from cars, lights in your home to even a pacemaker.
References Alan Grau, (2015), How to Build a Safer Internet of Things. https://spectrum.ieee.org/how-to-build-a-safer-internet-of-things CisoMag, (2019), Hackers Take Over Smart Home. https://cisomag.eccouncil.org/hackers-take-over-smart-home/ Erica Evans, (2020), Heres what you need to know about recent Amazon Ring hacking cases. Deseret News https://www.deseret.com/indepth/2020/1/3/21043653/amazon-ring-hacking-cases-doorbell-santa-claus-kids-bedroom-safe-lawsuit-security-camera-home-hacker